Windows Courses
Windows PowerShell
Java For Beginners
Category
- all-news (30)
- Category and Functor (8)
- Fraud (2)
- Java For Beginners (2)
- MoneyGram (1)
- News (2)
- Open Source (1)
- Protect Computer (1)
- Security (5)
- Snipping Tool: Faq (1)
- Source Code (1)
- Surveillance Software (1)
- VPS (1)
- Web Hosting (1)
- Webcam (1)
- Western Union (1)
- Windows 10 (1)
- Windows 7 (4)
- Windows 7 Faq (2)
- Windows 8 (1)
- Windows Accessories (1)
- Windows Fonts (1)
- Windows Registry (1)
- Windows Security (13)
- Windows Software (2)
- Windows Spyware (2)
- Windows utilities (1)
- Windows Virus (2)
- Windows Vista (3)
- Windows Wireless (1)
- Windows xp (1)
Math for Computing
Algo and Programmation
.
Web Languages
.
CMS and Web Design
-
Blog Archive
-
2016
(64)
-
décembre(32)
- Virus Protection not enough to keep your system safe
- Are You Protecting Your Computer?
- Annoying Spyware And Its Elimination
- Tips to Protect Your PC Files from External Attack
- The Warning signs of Online Fraud and How to avoid it
- Tips on Understanding the Dangers of Spyware and A...
- How to Install Windows TTF Fonts Automatically
- Is it time to step up to a full service VPS hostin...
- How to Run Windows on Mac: How to Install Windows ...
- How to Install Windows 7 in the Right Way
- How to Install Windows 7 on Virtual PC?
- Java First Program: Hello World
- 1 - Necessary Tools For Java Development
- How to Choose the Right Webcam Surveillance Software?
- Simple Steps - Protect your Computer Online
- Practical Use of Open Source Code Software
- 13 Comparisons of Vista vs Tiger
- 10 Reasons Why Vista is Much More Than a Spoon Ful...
- Fix Your Computer Registry
- What Is "Dllhost.exe"?
- 3 Ways That Can Help You to Remove Malware
- How Malware Works
- Protecting Your Business Website From Malwares
- Best Removal Tool For Windows
- Windows 7 Faq ( Configuring Windows )
- Windows Password Recovery Software
- Regutility - Best Registry Cleaner For Windows 10-...
- Ways to improve the signal Wifi 'wireless' in the ...
- Snipping Tool: frequently asked questions
- Use Snipping Tool to capture screen shots
- Windows 7 Faq ( Installation )
- Install Windows 7
- avril(31)
- mars(1)
-
décembre(32)
- 2015 (10)
Fourni par Blogger.
Data Bases
.
TICE & Multimedias
.
Archives du blog
-
▼
2016
(64)
-
▼
décembre
(32)
- Virus Protection not enough to keep your system safe
- Are You Protecting Your Computer?
- Annoying Spyware And Its Elimination
- Tips to Protect Your PC Files from External Attack
- The Warning signs of Online Fraud and How to avoid it
- Tips on Understanding the Dangers of Spyware and A...
- How to Install Windows TTF Fonts Automatically
- Is it time to step up to a full service VPS hostin...
- How to Run Windows on Mac: How to Install Windows ...
- How to Install Windows 7 in the Right Way
- How to Install Windows 7 on Virtual PC?
- Java First Program: Hello World
- 1 - Necessary Tools For Java Development
- How to Choose the Right Webcam Surveillance Software?
- Simple Steps - Protect your Computer Online
- Practical Use of Open Source Code Software
- 13 Comparisons of Vista vs Tiger
- 10 Reasons Why Vista is Much More Than a Spoon Ful...
- Fix Your Computer Registry
- What Is "Dllhost.exe"?
- 3 Ways That Can Help You to Remove Malware
- How Malware Works
- Protecting Your Business Website From Malwares
- Best Removal Tool For Windows
- Windows 7 Faq ( Configuring Windows )
- Windows Password Recovery Software
- Regutility - Best Registry Cleaner For Windows 10-...
- Ways to improve the signal Wifi 'wireless' in the ...
- Snipping Tool: frequently asked questions
- Use Snipping Tool to capture screen shots
- Windows 7 Faq ( Installation )
- Install Windows 7
-
▼
décembre
(32)
About Me
Google Ads
samedi 17 décembre 2016
By: Colleen Durkin
The Internet is a dangerous place for people as well as computer
systems. Every day there is a new threat that seeks to do harm to your
computer and the information contained within your hard drive. Many people believe that they are protected because they have anti-virus protection. Sadly, this is not the case. There are many threats that your anti-virus software will not protect you against. If you are surfing the Internet with just anti-virus protection then you may already have malicious programs running in your computer 'background', unknown to you and doing irreparable harm.
By: Alton Hargrave
Do you know what to look for in anti-virus software?
You just bought yourself a new computer! Can't wait to get it out of the box. Maybe you have had a computer before and maybe this is your second or third computer. And, you don't want to have all those problems you hear about. This is the time to think ahead and go for a positive online experience.
By: Allen Brown
Nowadays, you might have noticed of a threatening word "Spyware".
Spyware software is becoming annoyance for the companies. Spyware is
likely to be verified as a great damager to the companies. It is not so
noticeable like spam and virus assaults to the systems. Spyware could be
destructive and cause financial losses.Spyware is almost an invisible software programs that collects and transmits personal or company's important data through the Internet without being noticed. The transferred data could be used for smashing up your company's credit or might hard hit its profits. Spyware is also commonly acknowledged as Adware, Malware, Sneakware and Snoopware.
By: Paul Wilson
Essential to peace of mind is protecting the PC and your online privacy.
When connected to the web, your work and data is open to attacks of
various kinds including harmful downloads. A simple game, picture, or
program may be the vehicle for malevolence. So, you need to check
whether every file that you download, open, or save, is safe or whether
there are irregularities of any kind.
By: Donald Lee
The number may seem grim for Web-based commerce. In 2004 in the Unites
States alone, computer users logged in more than 207,000 Internet fraud
reports to the U.S. Internet Crime Complaint Center. If you look hard at
this number, you may be astounded, and a good bit frightened, by the
implication. You may ask, "Is it really safe to buy and sell at an
online site?"
By: Paul Wilson
Money is the very crux of adware and spyware. These pose several problems and are a security risk.Adware is a program that displays advertisements on the computer whether you want them or not. They are not just connected to particular websites or free software but are programmed to start up whenever your computer is switched on.
mercredi 14 décembre 2016

The technical definition of a font is a complete character set of
a single size and style. Most fonts are in truetype format, or TTF. If
you use the Ubuntu operating system, it may be difficult to install TTF
fonts on your computer because they were designed to be used on Windows
operating systems.
Although you can install TTF fonts on your Ubuntu operating system manually, you will have to do it over and over again every time you want to install a new TTF font, which can become very tedious. You can, however, automate the process of installing TTF fonts on your Ubuntu system. Here are two step-by-step tutorials that will walk you through the installation process.
Although you can install TTF fonts on your Ubuntu operating system manually, you will have to do it over and over again every time you want to install a new TTF font, which can become very tedious. You can, however, automate the process of installing TTF fonts on your Ubuntu system. Here are two step-by-step tutorials that will walk you through the installation process.
For anybody who is fed up with the inadequate overall performance of their shared web server but not yet in a position to step up to a costly dedicated server than the most suitable option available for you would be a Virtual Private Server (VPS).
The two main forms of VPS solutions are managed and unmanaged VPS services. Managed VPS hosting services are similar in a lot of ways to hosting that is shared. You'll receive skilled pros who will take care of any issues with your hosting server which could develop.

How to Install Windows on Mac in Just 3 Steps!
Doesn't it stink when you're a Mac user and you suddenly need a Microsoft Windows program? I don't know why I hate it so, but I am not alone or I wouldn't be writing this right now. In this Windows controlled world we lovers of Mac must face the facts sometimes, and that is that there are always going to be times when we will need to resort to using Windows.
Doesn't it stink when you're a Mac user and you suddenly need a Microsoft Windows program? I don't know why I hate it so, but I am not alone or I wouldn't be writing this right now. In this Windows controlled world we lovers of Mac must face the facts sometimes, and that is that there are always going to be times when we will need to resort to using Windows.
Windows 7 is the latest offering from Microsoft Corporation after their recent release of Windows Vista.
Here is a summarization of various steps you need to follow if you want to know how to install windows 7. The steps are:
• The first thing you need to do is check whether your desktop or laptop is compatible for windows 7 to run or not. Windows 7 is a very powerful operating system and therefore requires some minimum hardware requirements for it to operate smoothly. Microsoft recommends systems with at least 1 GHz CPU and 1GB RAM. Therefore, it is advisable to download and run special free software which checks you system for windows 7 compatibility. If you already have windows vista installed on your system chances are you won't need any upgradation but it is always good to run this check before you start the process of installation.
• The next step is to choose an edition. There are 3 editions available: Home Premium, Professional and Ultimate. Choose an edition that fulfills your needs. The prices of all the editions are different. So choose carefully.
• Now you have to decide whether you want to buy 32 bit windows 7 or 64 bit windows 7. Although all the new systems come equipped with 64 bit based processors it is still advisable to check your system's properties and then choose accordingly.
• Installing a new operating system is like giving your desktop or laptop a new life. Suppose if you are installing a new operating system and something goes wrong or the power is gone. You will end up losing a lot of data. Therefore, it is always advisable to take the back up of your data before you begin the process of installation. Many times it is not possible to back up all the data so it is good to at least back up all the important stuffs.
• After you have done all the necessary preparation it is time to start with the installation. There are two options. Either you can upgrade if you already have a windows operating system installed or you can install if your computer has never tasted the sweet taste of windows.
• After the installation has begun make sure you are connected to the internet. At any time windows may attempt to download any updates from the internet. The whole process of installation will take 10 to 20 minutes depending on your system's hardware. After the installation is complete your computer will restart with your new windows 7.
Follow these easy steps carefully if you want to know how to install windows 7.
All the best!
Here is a summarization of various steps you need to follow if you want to know how to install windows 7. The steps are:
• The first thing you need to do is check whether your desktop or laptop is compatible for windows 7 to run or not. Windows 7 is a very powerful operating system and therefore requires some minimum hardware requirements for it to operate smoothly. Microsoft recommends systems with at least 1 GHz CPU and 1GB RAM. Therefore, it is advisable to download and run special free software which checks you system for windows 7 compatibility. If you already have windows vista installed on your system chances are you won't need any upgradation but it is always good to run this check before you start the process of installation.
• The next step is to choose an edition. There are 3 editions available: Home Premium, Professional and Ultimate. Choose an edition that fulfills your needs. The prices of all the editions are different. So choose carefully.
• Now you have to decide whether you want to buy 32 bit windows 7 or 64 bit windows 7. Although all the new systems come equipped with 64 bit based processors it is still advisable to check your system's properties and then choose accordingly.
• Installing a new operating system is like giving your desktop or laptop a new life. Suppose if you are installing a new operating system and something goes wrong or the power is gone. You will end up losing a lot of data. Therefore, it is always advisable to take the back up of your data before you begin the process of installation. Many times it is not possible to back up all the data so it is good to at least back up all the important stuffs.
• After you have done all the necessary preparation it is time to start with the installation. There are two options. Either you can upgrade if you already have a windows operating system installed or you can install if your computer has never tasted the sweet taste of windows.
• After the installation has begun make sure you are connected to the internet. At any time windows may attempt to download any updates from the internet. The whole process of installation will take 10 to 20 minutes depending on your system's hardware. After the installation is complete your computer will restart with your new windows 7.
Follow these easy steps carefully if you want to know how to install windows 7.
All the best!
Author recommends Tech-FAQ for more information on topics such as How to Install Windows 7 and How to activate Windows 7. You may visit for more details.
Article Source:
http://EzineArticles.com/expert/Dennis_Moore_Hopkins/516335
Article Source: http://EzineArticles.com/4863666
If you are running Windows Vista and planning to upgrade latest Windows 7 operating system then VPC is the best way to install. It is recommended to use Virtual PC to install Windows 7 on already running Windows Vista machine. For those who are not aware, Microsoft Virtual PC allows you run multiple operating systems simultaneously on the same computer system.
mardi 13 décembre 2016
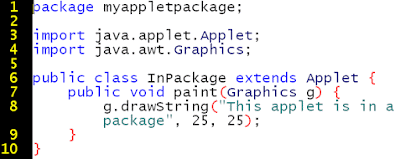
Creating Your First Application
Your first application,
HelloWorldApp, will simply display the greeting "Hello World!" To create this program, you will:-
Create an IDE projectWhen you create an IDE project, you create an environment in which to build and run your applications. Using IDE projects eliminates configuration issues normally associated with developing on the command line. You can build or run your application by choosing a single menu item within the IDE.
1 - The JDK development environment
Before starting the Java development, you must at first prepare your machine by installing the necessary software! For this you must download the following tools:
ii) JRE (Java run time environment) tool required for the execution of all java program
By: Dan Crane
Many people want to have some kind of spy equipment for better home
security. However, besides wireless spy cameras, VCR or DVR systems,
there is also special software used to control those surveillance
gadgets. Large companies use professional security systems along with already built in (embedded digital video recorder or PC based DVR soft) spy camera control software. But what about smaller guys? Do you also have to spend thousands of dollars for professional spy security system and software to feel safe and secure in your house? And the answer is not necessarily.
By: Nam Sss
So you've bought your computer and want to get online? It's not as simple as connect the wire and off you go these day's. The internet is a weird and wonderful place as long as you can control what you do.
That's why you need to protect yourself. These can be done in a number of very simple steps. This article will get you started but you should always try to be smart when your surfing the net!
By: Roberto Sedycias
As we started the project of our web site, we knew that the proprietary
software costs would be too high for our financial resources. Our only
option then was to make use of Open Source Code softwares.However, within the Open Source Code there are lots of softwares to choose from, and it´s up to the system analyst/programmer to pick the ones that best suit the project goals.
lundi 12 décembre 2016
By: Paul Wilson
Competitive and fast are two terms that are applicable to the world of
computers. Constantly changing and evolving computer systems bring many
advantages to the users and techies alike. The race for supremacy
between the yet to be launched Vista (scheduled for 2006) and Mac OSX
Tiger began in 2003 with Microsoft's announcements of plans for an
integrated desktop search functionality in Windows Vista.
By: Paul Wilson
Every new operating system comes with advanced and much improved
features. What is exciting to some is not so to others. Basically within
a new system each user has his or her own individual preferences.
Windows Vista or Longhorn as it was first known is a replacement for XP
and is the "new" desk operating system scheduled to be launched by
December 2006.
By: Tim Lee
The Windows Registry System
Basically, for all windows users, one of the most important things in a computer that needs backup is the windows registry.In windows, the registry system stores all of your information in your computer. These are placed in a database system where certain data about the user profile, configuration settings, and installed programs are recorded.
dimanche 11 décembre 2016
The file was published at 7/13/2009 4:43:52 PM, and is usually located in C:WindowsSystem32dllhost exe. Once active, the file will occupy 7168 KB of memory usage.
If the memory usage of the file showed in the Task Manager is over 1698265 bytes, then there may be a virus (for example, Constructor:BAT/DBCK or Trojan Program:Win32/AdvancedCleaner) on your machine. This file should be replaced immediately with a clean one.
Malware is a software that is made specifically to damage or disable computers and computer systems. Its name is actually derived from the term malicious software and it seeks to gain access to the computer without the owner knowing anything about it. The owner may not know how or when it got into the computer, but they will find out it did when the computer starts acting up, running slowly or there is a big jump in the amount of ads that appear.
With ecommerce sites on the rise and over a million new stains of
malware developed every day, protecting your business site from attacks
from viruses and malware has become a priority now. Hackers are
continually creating various new means to gather credit card details and
other personal information from their online transactions. Adopting the
best security practices has now become very crucial for merchants. It
has become essential to install the proper website protection to stop
various attacks and today, there are several programs that can be used
to protect your computer from such malware attacks.
Best Removal Tool
Uninstall Tool
Do you want to completely Uninstall Tool that is half-installed/uninstalled incorrectly?
Would you like to uninstall software which is not in the currently installed programs list so you can not uninstall it through the standard Windows Add/Remove Programs?
Have you been afraid of the Windows system errors or crash when you uninstall software manually?
Best Removal Tool can enable you to completely uninstall software that the standard Windows Add/Remove Programs can’t uninstall.
Do you want to completely Uninstall Tool that is half-installed/uninstalled incorrectly?
Download software removal tool to uninstall software and remove software Buy software removal tool to uninstall software and remove software.
Do you want to completely Uninstall Tool that is half-installed/uninstalled incorrectly?
Would you like to uninstall software which is not in the currently installed programs list so you can not uninstall it through the standard Windows Add/Remove Programs?
Have you been afraid of the Windows system errors or crash when you uninstall software manually?
Best Removal Tool can enable you to completely uninstall software that the standard Windows Add/Remove Programs can’t uninstall.
Do you want to completely Uninstall Tool that is half-installed/uninstalled incorrectly?
Download software removal tool to uninstall software and remove software Buy software removal tool to uninstall software and remove software.
samedi 10 décembre 2016
Windows 7 Faq ( Configuring Windows )
2.1. Configuring the display
- How to quickly configure a dual screen display or video projector ?
To quickly configure the dual display type, you can use the [Windows] + [P] keyboard shortcut.
To quickly configure the dual display type, you can use the [Windows] + [P] keyboard shortcut.
- How do I change the screen resolution ?
To change the screen resolution (or screens for multiple displays), right-click on the desktop and select Resolution.
- Where are Windows default wallpapers located ?
The wallpapers included by default with Windows are located in the folder C: \ Windows \ Web \ Wallpaper
Wallpapers by country (eg Canada / France for the French version of Windows) are located in the folder C: \ Windows \ Globalization \ MCT. You will find several wallpapers corresponding to the chosen country.
Wallpapers by country (eg Canada / France for the French version of Windows) are located in the folder C: \ Windows \ Globalization \ MCT. You will find several wallpapers corresponding to the chosen country.
- How to enable or disable Aero Peek?
The Aero Peek feature allows you to preview the desktop,by flying over the translucent button at the bottom right of the screen.
To disable this function, right-click the translucent button beside the clock and uncheck the "Stealth Switch to Desktop" option.
To disable this function, right-click the translucent button beside the clock and uncheck the "Stealth Switch to Desktop" option.
- How to quickly activate / deactivate an external display (video projector, screen) ?
How to activate / deactivate an external display (projector, screen), make [Windows] + [P] and choose the desired mode (no external display, duplicate, expand or external display only).
- How do I change the login screen background ?You can choose the image to display in the background of the Windows 7 login screen.
To do this, you can use the free Windows 7 Logon Background Changer tool downloadable here.
To do this, you can use the free Windows 7 Logon Background Changer tool downloadable here.
2.2. System requirements
- How do I change the date and time ?
To change the system date and time, right-click the time in the taskbar. Then choose Adjust Date / Time.
In the window that opens, click the Change Date and Time button (you must have administrator privileges to perform this action). Use the calendar in the left part of the window to change the current date and use the input box below the clock to change the current time. Confirm by clicking the Ok button.
In the window that opens, click the Change Date and Time button (you must have administrator privileges to perform this action). Use the calendar in the left part of the window to change the current date and use the input box below the clock to change the current time. Confirm by clicking the Ok button.
- How do I change the environment variables ?
To change the environment variables, follow these steps :
Right-click on Computer
Click Properties
The System window opens.
In the left column, click Advanced System Settings
The System Properties window opens.
Click the Environment Variables button
Right-click on Computer
Click Properties
The System window opens.
In the left column, click Advanced System Settings
The System Properties window opens.
Click the Environment Variables button
At the top, you can set environment variables for your user account only. In the lower part of the window you can define the system environment variables common to all users on the computer.
- How to add a new font in Windows 7 ?
Windows comes with a number of fonts already installed. To add more, download a font file to your hard drive. Right-click the font file and choose "Install."
You can also install a font by dragging it to the Fonts page in Control Panel.
You can also install a font by dragging it to the Fonts page in Control Panel.
To access the Fonts page, open the Start menu> Control Panel> Appearance and Personalization> Fonts.
RegUtility is a multi-awarded winning Windows Registry Cleaner.
RegUtility™ is an all-in-one system utility to safely scan, clean up, maintain, optimize and speed up your PC. RegUtility™ is the safest and most trusted solution to clean registry,fix and optimize your PC, free it from registry errors and fragmented entries.mercredi 7 décembre 2016
To improve the signal Wifi wireless home
If the Windows operating system ever notifies you about the weak Wi-Fi signal, it may mean that your connection is not as fast or credibility wanted. Even worse, you may lose your connection entirely in some parts of the Almenzl.lma If you want to strengthen your wireless network signal (WLAN), you can try these tips to expand the wireless network range and improve the performance and the speed of the wireless network.
Here are answers to some common questions about Snipping
Tool and snips.
How do I use Snipping Tool?
To capture a snip,
do the following:
- Click on the Snipping Tool from the start menu.
- Click the arrow next to the New button, select Free-form Snip, Rectangular Snip, Window Snip, or Full-screen Snip from the list, and then select the area of your screen that you want to capture.
The captured area of the screen appears
in the mark-up window, where you can write or draw on it, save it, and send it
to someone in an e‑mail. For more information, see Use
Snipping Tool to capture screen shots.
How do I save snips?
When you capture a
snip, it is automatically copied to the Clipboard
so that you can quickly paste it into a document, e‑mail, or presentation.
You can also save a snip as an HTML, PNG, GIF, or JPEG
file. After you capture a snip, you can save it by clicking the Save Snip
button in the mark-up window.
Why does a URL appear
below my snip when I save it?
A URL appears when
you capture a snip from a browser window
and save it as an HTML file. To turn off
this option:
- Click on the Snipping Tool from the start menu.
- Click Options.
- In the Snipping Tool Options dialog box, clear the Include URL below snips (HTML only) check box, and then click OK.
Can I remove or change the
color of the ink in the outline that's used to capture snips?
Yes. Here's how:
- Click on the Snipping Tool from the start menu.
- Click Options.
- In the Snipping Tool Options dialog box, do one of the following:
- To remove the outline, clear the Show selection ink after snips are captured check box, then click OK.
- To change the color of the outline, select a color from the Ink color list, and then click OK.
Why are my snips sent as an
e‑mail attachment even though I didn't select E‑mail Recipient (as attachment)?
Snips are sent as an e‑mail attachment if you send a
plain-text or rich-text e‑mail. To paste a snip into an e‑mail message, specify
HTML as the message format in your e‑mail
program.
Can I capture a snip of a
menu, such as a shortcut menu or the Start menu?
Yes. Here's how:
- Click on the Snipping Tool from the start menu.
- Press Esc, and then open the menu that you want to capture.
- Press Ctrl+PrtScn.
- Click the arrow next to the New button, select Free-form Snip, Rectangular Snip, Window Snip, or Full-screen Snip from the list, and then select the area of your screen that you want to capture.
You can use
Snipping Tool to capture a screen shot, or snip,
of any object on your screen, and then annotate, save, or share the image.
You can capture
any of the following types of snips:
- Free-form Snip. Draw a free-form shape around an object.
- Rectangular Snip. Drag the cursor around an object to form a rectangle.
- Window Snip. Select a window, such as a browser window or dialog box, that you want to capture.
- Full-screen Snip. Capture the entire screen.
After you
capture a snip, it's automatically copied to the Clipboard
and the mark-up window. From the mark-up window, you can annotate, save, or
share the snip. The following procedures explain how to use Snipping Tool.
To
capture a snip
- Click on the Snipping Tool from the start menu.
- Click the arrow next to the New button, select Free-form Snip, Rectangular Snip, Window Snip, or Full-screen Snip from the list, and then select the area of your screen that you want to capture.
To
capture a snip of a menu
If you want to
capture a snip of a menu, such as the Start menu, follow these steps:
- Click on the Snipping Tool from the start menu.
- After you open Snipping Tool, press Esc, and then open the menu that you want to capture.
- Press Ctrl+PrtScn.
- Click the arrow next to the New button, select Free-form Snip, Rectangular Snip, Window Snip, or Full-screen Snip from the list, and then select the area of your screen that you want to capture.
To
annotate a snip
- After you capture a snip, you can write and draw on or around the snip in the mark-up window.
To
save a snip
- After you capture a snip, click the Save Snip button in the mark-up window.
- In the Save As dialog box, enter a name for the snip, choose a location where to save the snip, and then click Save.
To
share a snip
- After you capture a snip, click the arrow on the Send Snip button, and then select an option from the list.
For more
information about Snipping Tool, see Snipping Tool:frequently asked questions.
Inscription à :
Articles (Atom)

![Prior to the introduction of web hosting services, in order to host a website on the internet, an individual or company would need their own computer or server.[1] In 1991, restrictions on using the world wide web for commercial purposes was lifted[2], allowing companies to have a presence on the internet. The Commercial Internet Exchange Association (CIX) was formed that year with the goal of providing internet access without restrictions on what kind of traffic was being sent. Companies began to offer to host users websites on their own servers, without the client without needing to own the necessary infrastructure required to operate the website. VPS hosting, web hosting](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiZDwTZT1_dQGlnbdoJSfzEWSm61-U6gNnlWf0D0DSemmIhm2o8vgaNgobuUAgbWBcq27IlkQL6saQK9ZbTs2YPm18ypjfHZ_yxN6_-MVEcChXdmOjeCc9ccXb0o7CRqbovy7jocn00Kh6t/s640/linux-vps-hosting-stariz-dot-net.jpg)